Category: Blog
-
![[LinuxLog 000]: Linux on Laptop as Primary OS](https://ZaidPirwani.com/wp-content/uploads/2014/08/gparted-snapshot-672x323.png)
[LinuxLog 000]: Linux on Laptop as Primary OS
Finally decided to ditch my dying(dead) Win8 and install something else, wanted to install Windows7 but not having a 64-bit copy and wanting to try out Linux as a primary OS, decided to install Linux Mint Debian, not much of a selection as this was the ISO which I had on my system already. My…
-
Leaky Code…
I had heard lots and lots about leaky code so far, but never actually learned about it or read about it until tonight… so here it is below: a sample of LEAKY CODE (source: Wikipedia) #include <stdlib.h> void function_which_allocates(void) { /* allocate an array of 45 floats */ float * a = malloc(sizeof(float) * 45);…
-

EiD: Hugs, Eidi and GUNS
First and foremost; EID MUBARAK TO ALL… I have been awfully lazy this Eid and didn’t even send Eid Greetings SMS to anyone except a select few. If someone looked down on Karachi, PK via satellite on Eid days, he would see Large gatherings of Muslims Hugging each other like its the last time they’ll…
-

Bottle Cap Runaway Car….!
I have a little cousin, in 7th grade… he has recently been getting more and more interested in hacking and tinkering his toys, taking them apart and playing with the LEDs and motors inside. When I met him last week, he showed me this car that he made, all by himself. he was like kinda…
-
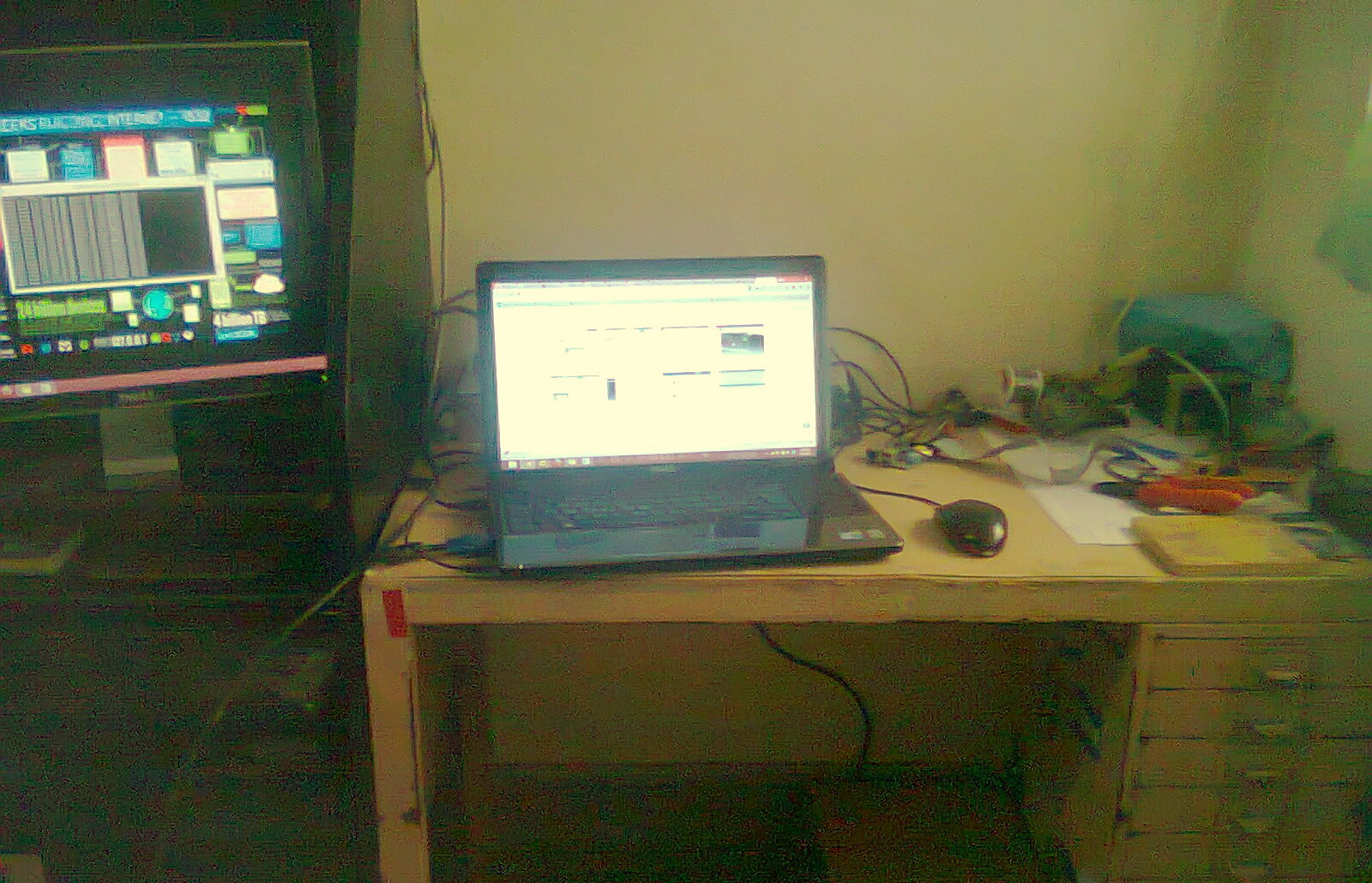
Workstation @ Home
A laptop, a desktop PC, one Raspberry Pi and a soldering station plus loads of electronic components right in my reach in all those drawers…